- Published on
Harnessing AWS IAM and Terraform for Enhanced Cybersecurity
- Authors
- Name
- Ted
- @supasaf
Alright, let's talk about IAM. Imagine your AWS account is a giant, expensive castle. You've got treasure rooms (your S3 buckets), secret laboratories (your EC2 instances), and a whole lot of important stuff you don't want just anyone messing with.
Now, how do you manage the keys? In the old days of manual cloud management, it was chaos. You’d have people sharing the master key, sticky notes with passwords under keyboards, and that one intern who somehow got permission to delete the entire production database. Every time you gave someone access, you were basically closing your eyes, handing them a key, and praying they didn't burn the castle down.
This is where AWS Identity and Access Management (IAM) comes in. It’s the official rulebook for who can enter the castle and what they're allowed to do. And when you combine it with Terraform, you turn that chaotic mess of keys into a neat, automated, and auditable system. You become the wise, all-seeing castle warden instead of the panicking guard running around with a giant key ring.
AWS IAM Users: The Bouncers at Your Cloud Nightclub
First up, IAM Users. Think of these as the individual ID cards for every person or service that needs to get into your cloud. Giving everyone their own user account instead of sharing one is Security 101. It's like having a bouncer at the door who checks everyone's ID instead of just letting in anyone who says, "Bob sent me."
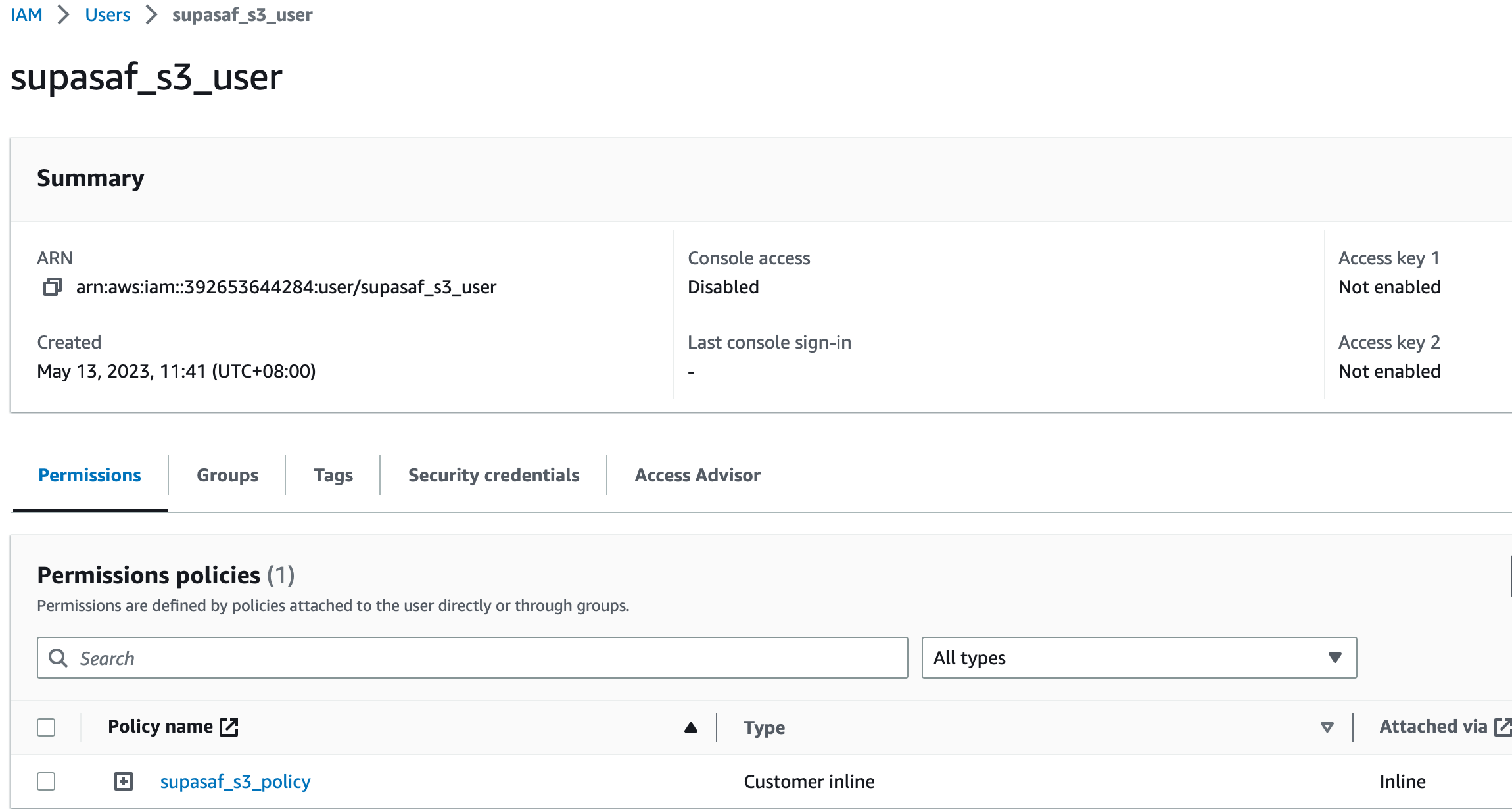
With Terraform, creating these users is a piece of cake. Here, we're creating a user named supasaf_s3_user and giving them a very specific permission slip (an "identity policy") that says they can only list the contents of one specific bucket. They can't delete it, they can't empty it—they can just look at the list of files. This is called the "Principle of Least Privilege," which is a fancy way of saying: "Don't give someone the key to the whole castle when they just need to use the bathroom."
resource "aws_iam_user" "supasaf_s3_user" {
name = "supasaf_s3_user"
}
resource "aws_iam_user_policy" "supasaf_s3_policy" {
name = "supasaf_s3_policy"
user = aws_iam_user.supasaf_s3_user.name
policy = jsonencode({
Version = "2012-10-17",
Statement = [
{
Action = ["s3:ListBucket"],
Effect = "Allow",
Resource = ["arn:aws:s3:::supasaf-demo"]
},
],
})
}
After you run this, you'll see your shiny new user in the AWS console, all ready to go.
Resource Policies: Putting a Lock on the Actual Treasure Chest
Now, an identity policy is like a note on a user's ID card saying what they're allowed to do. A Resource Policy is different. It's a magical lock you put directly on the resource itself—like on the door of your S3 treasure chest. This lock has its own set of rules, saying, "I don't care what your ID says, only these specific people can open this door."
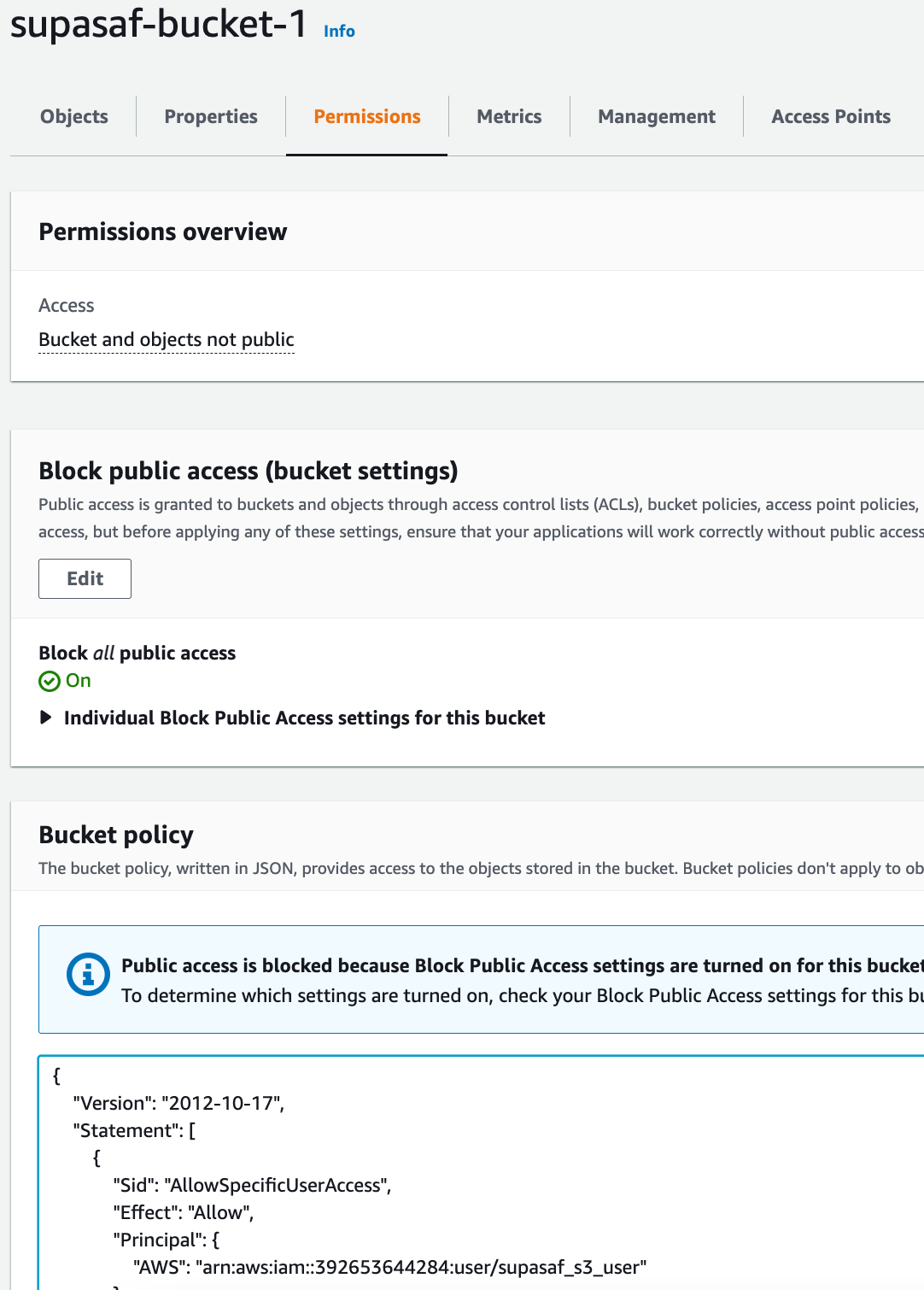
This is great for double-checking your security. Here, we're attaching a policy directly to our S3 bucket that explicitly allows our supasaf_s3_user to list its contents and get objects. It’s an extra layer of certainty.
resource "aws_s3_bucket" "bucket" {
bucket = "supasaf-bucket-1"
}
data "aws_iam_policy_document" "bucket_policy" {
statement {
sid = "AllowSpecificUserAccess"
principals {
type = "AWS"
identifiers = ["arn:aws:iam::392653644284:user/supasaf_s3_user"]
}
actions = [
"s3:ListBucket",
"s3:GetObject"
]
resources = [
"${aws_s3_bucket.bucket.arn}",
"${aws_s3_bucket.bucket.arn}/*"
]
}
}
resource "aws_s3_bucket_policy" "bucket_policy" {
bucket = aws_s3_bucket.bucket.id
policy = data.aws_iam_policy_document.bucket_policy.json
}
You can check your work by looking at the bucket's "Permissions" tab and admiring your handiwork.
IAM Groups: Stop Making Individual Keys!
Okay, managing permissions for one user is easy. But what about 20 developers? Or 50 data analysts? If you give each one a custom set of permissions, you'll go insane. You'll make mistakes, and mistakes lead to security holes.
Enter IAM Groups. A group is just a collection of users. You attach the permission policies to the group, not the individual users. When a new developer joins, you just add them to the "Developers" group. Done. They instantly get all the right permissions. When they leave, you remove them from the group. It's clean, simple, and saves you from a world of pain.
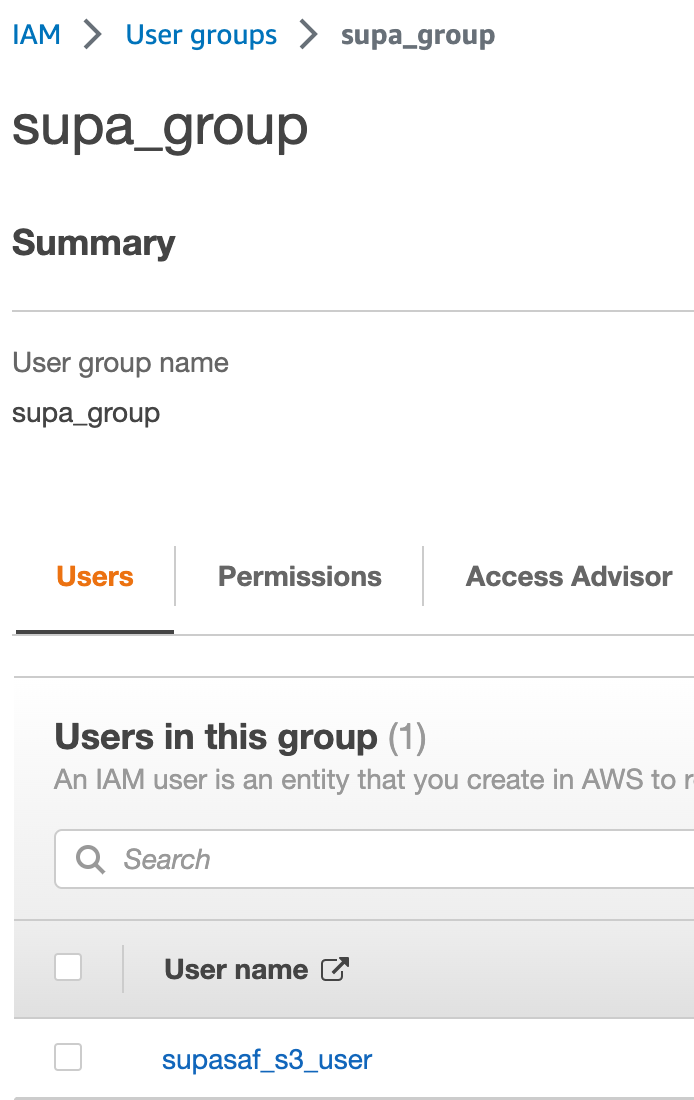
Here, we create a group for S3 power users and add our one user to it. Imagine doing this for dozens of people.
resource "aws_iam_group" "supa_group" {
name = "supa_group"
}
resource "aws_iam_group_policy" "supa_group_policy" {
name = "supa_group_policy"
group = aws_iam_group.supa_group.id
policy = <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:Get*",
"s3:List*",
"s3:Put*",
"s3:Delete*"
],
"Resource": "arn:aws:s3:::supasaf-bucket-1/*"
}
]
}
EOF
}
resource "aws_iam_group_membership" "supasaf_membership" {
name = "supasaf_membership"
users = [
"supasaf_s3_user",
]
group = aws_iam_group.supa_group.name
}
And voilà, the group appears, ready to streamline your permissions.
IAM Roles: The Magic Valet Key
This is my favorite part. IAM Roles are the cleverest tool in the box. A role is not a person. It's a hat. Anyone (or any service) who is allowed to can temporarily put on that hat to get a specific set of permissions to do a specific job.
Think of it like a valet key for your car. The key can start the engine and move the car, but it can't open the trunk. A valet (your EC2 instance, or another user) can assume the role of the valet key to park your car, but they don't get the master keys to your life. This is HUGE for security because the credentials are temporary. There are no long-term secret keys lying around waiting to be stolen.
In this script, we create a role that our supasaf_s3_user can temporarily assume. When they assume it, they get the power to put objects in our S3 bucket.
resource "aws_iam_role" "supa_s3_role" {
name = "supa_s3_role"
assume_role_policy = jsonencode({
Version = "2012-10-17",
Statement = [
{
Action = "sts:AssumeRole",
Principal = {
AWS = "arn:aws:iam::392653644284:user/supasaf_s3_user"
},
Effect = "Allow",
},
],
})
}
resource "aws_iam_role_policy" "supa_s3_role_policy" {
name = "supa_s3_role_policy"
role = aws_iam_role.supa_s3_role.id
policy = jsonencode({
Version = "2012-10-17",
Statement = [
{
Action = ["s3:PutObject"],
Effect = "Allow",
Resource = ["arn:aws:s3:::supasaf-bucket-1/*"]
},
],
})
}
A quick search in the console confirms our new role is ready to be worn.
The Takeaway: Stop Handing Out Master Keys!
So there you have it. Using Terraform to manage your AWS IAM isn't just a "best practice"; it's a sanity-saver. By defining all your permissions in code, you get a clear, auditable, and repeatable way to control who touches what in your cloud castle. You stop guessing and start knowing.
No more sticky notes. No more "whoops, I deleted production." Just clean code and a much, much smaller chance of getting that dreaded 3 AM call. Until next time, stay secure, and for heaven's sake, stop sharing keys!