- Published on
Encrypting DynamoDB with AWS KMS: A Secure and Easy Guide
- Authors
- Name
- Ted
- @supasaf
Let's talk about your data. Think of it as your secret diary or your grandma's legendary cookie recipe. You wouldn't just leave it sitting on the coffee table for anyone to read, would you? Of course not. You'd lock it up. In the cloud, this process of locking up your data is called encryption.
Amazon DynamoDB is a fantastic database—it's fast, scalable, and you don't have to worry about managing servers. By default, Amazon puts a basic lock on all your data, which is nice of them. But here's the thing: you don't control that lock or its key.
For true security, you want to be the one holding the keys to your own kingdom. This is where AWS Key Management Service (KMS) comes in. It lets you create your own cryptographic keys, giving you full control over who can "unlock" your data and when. When you use your own key, you're upgrading from the standard diary lock to a high-security bank vault door that only you control.
And with Terraform, we can build this entire setup automatically.
Step 1: Forge Your Own Master Key
Before we can lock our diary, we need a key! Our first step is to ask KMS to create a brand new, unique Customer Master Key (CMK) for us. We're not going to use a key that anyone else has. This one is ours.
With Terraform, telling KMS to create a key is laughably simple.
resource "aws_kms_key" "dynamodb_key" {
description = "KMS key for encrypting DynamoDB tables"
deletion_window_in_days = 7
}
output "kms_key_id" {
value = aws_kms_key.dynamodb_key.id
}
After running terraform apply, you can pop over to the AWS console and admire your shiny new key. It exists! It's real!
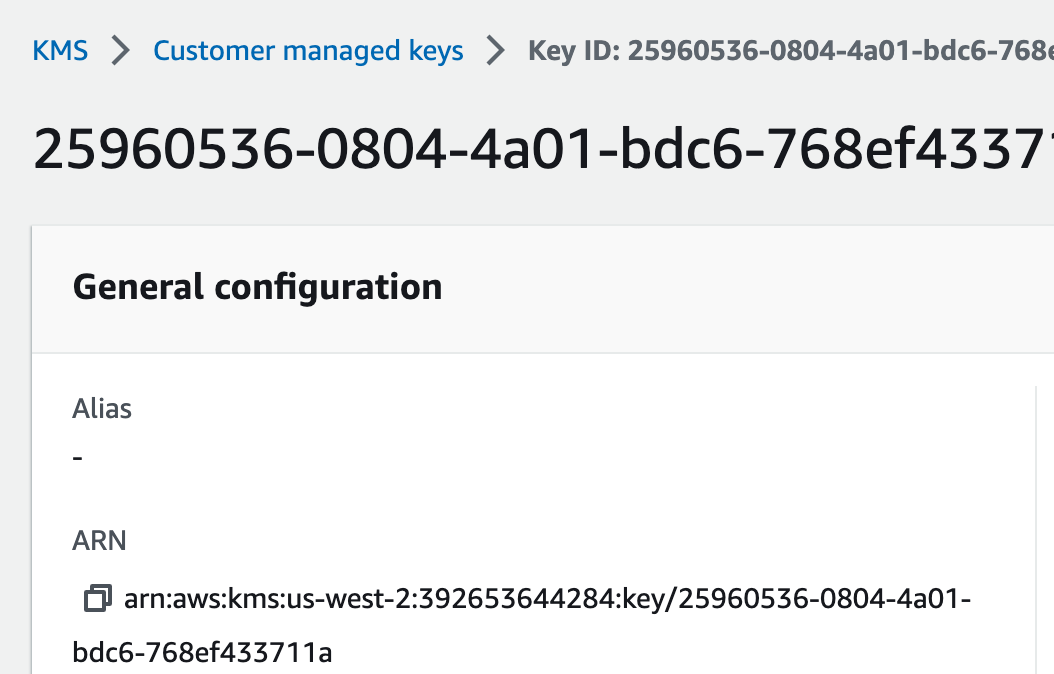
Step 2: Build the Locked Diary (The Encrypted Table)
Now that we have our super-secure key, we need a diary to lock with it. Let's create a DynamoDB table.
The magic happens in the server_side_encryption block. This is where we tell DynamoDB, "Hey, don't use your standard, boring lock. I brought my own. Use this specific key we just made."
resource "aws_dynamodb_table" "encrypted_table" {
name = "my-encrypted-table"
billing_mode = "PAY_PER_REQUEST"
hash_key = "id"
read_capacity = 5
write_capacity = 5
attribute {
name = "id"
type = "S"
}
server_side_encryption {
enabled = true
kms_key_arn = aws_kms_key.dynamodb_key.arn
}
}
output "dynamodb_table_name" {
value = aws_dynamodb_table.encrypted_table.name
}
Let's add an item to our new table just to make sure it works.
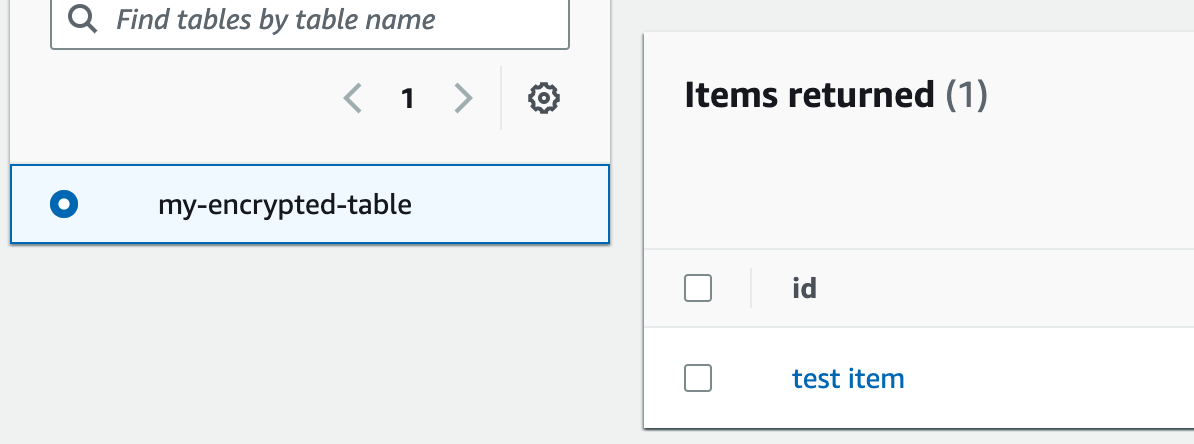
Looks good! Our data is now stored in the table, and it's encrypted with the key that only we control.
The Real Security Win: Why This Is So Cool
So what's the big deal? Let me show you.
Imagine you have a database administrator named dynamo_test_user. You give this user the AmazonDynamoDBFullAccess policy, which basically makes them a god of DynamoDB. They can create, delete, and read from any table in the account.
So, this all-powerful user tries to scan our new, encrypted table. What happens?
ACCESS DENIED.
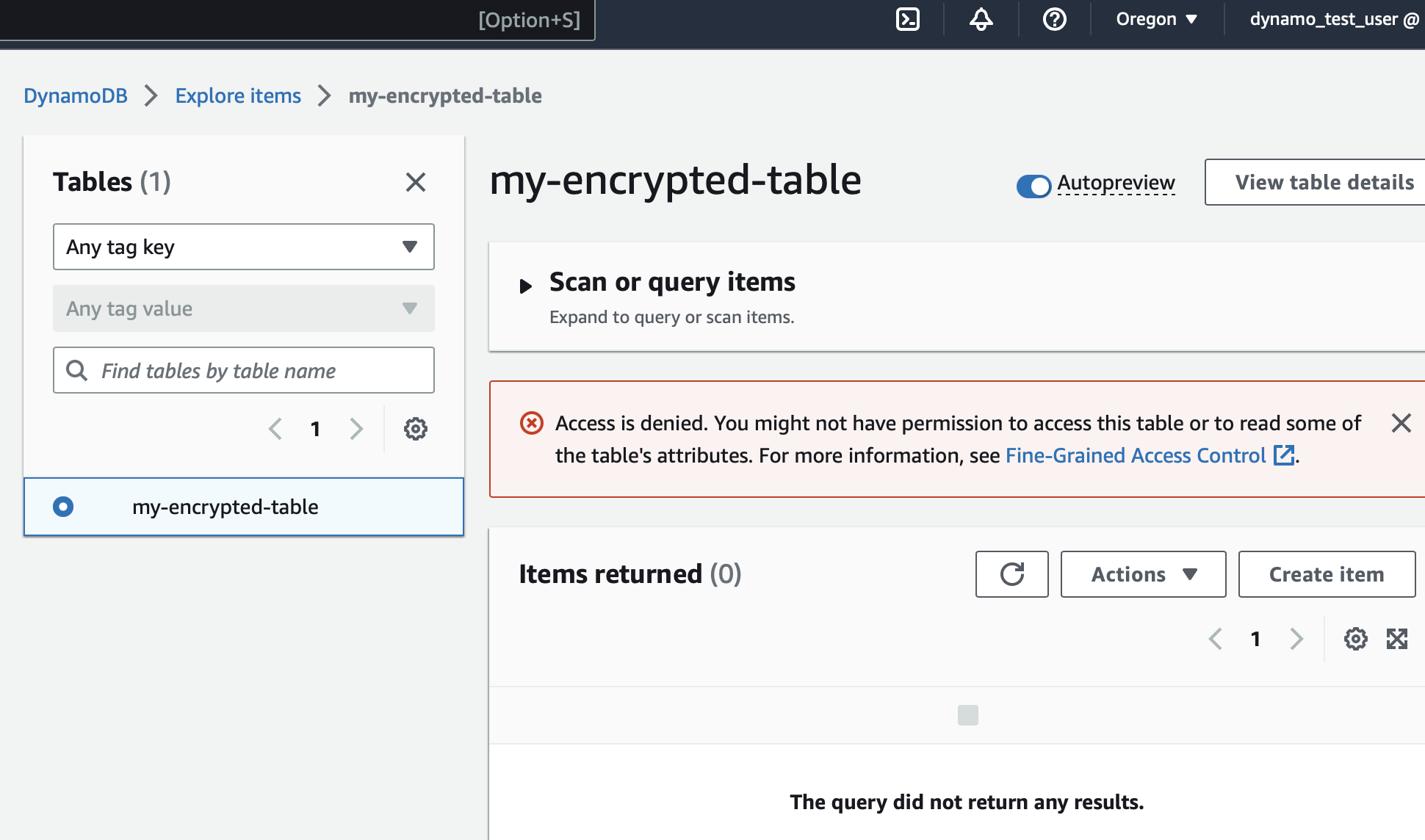
But... why? They have full access to DynamoDB!
This is the beautiful part. Because the table is encrypted with our CMK, a user needs two separate permissions to read the data:
- Permission to access DynamoDB (which they have).
- Permission to use the KMS key that locks the table (which they do not have).
When our user tried to read the table, DynamoDB turned to KMS and said, "Hey, can you unlock this data for dynamo_test_user?" And KMS, acting as the ultimate security guard, checked its list, saw the user wasn't on it, and replied, "Absolutely not."
This is a powerful security concept called separation of duties(SOP). Your database admins are no longer automatically your data admins. Just because they can manage the database doesn't mean they can read the sensitive information inside it. You have effectively separated the control of the infrastructure from the control of the data itself.
The Takeaway: Control Your Keys, Control Your Data
Using a customer-managed KMS key to encrypt your DynamoDB tables is one of the smartest and easiest security upgrades you can make. It moves you from a position of "I hope my data is safe" to "I know my data is safe, because I'm the only one with the key."
By defining this all in Terraform, you get a repeatable, auditable, and automated way to enforce one of the most important principles in cybersecurity. So go on, start forging your own keys and locking your own diaries. Your future, more secure self will thank you for it.